One of the best features of the ZDLRA is the ability to dynamically create a full Keep backup and send it to Cloud (ZFSSA or OCI) for archival storage.
Here is a great article by Oracle Product Manager Marco Calmasini that explains how to use this feature.
In this blog post, I will go through the RACLI steps that you execute, and explain what is happening with each step
The documentation I am started with is the 21.1 administrators Guide which can be here. If you are on a more current release, then you can find the steps in chapter named "Archiving Backups to Cloud".
Deploying the OKV Client Software
To ensure that all the backup pieces are encrypted, you must use OKV (Oracle Key Vault) to manage the encryption keys that are being used by the ZDLRA. Even if you are using TDE for the datafiles, the copy-to-cloud process encrypts ALL backup pieces including the backup of the controlfile, and spfile which aren't already encrypted.
I am not going to go through the detailed steps that are in the documentation to configure OKV, but I will just go through the high level processes.
The most important items to note on this sections are
- Both nodes of the ZDLRA are added as endpoints, and they should have a descriptive name that identifies them, and ties them together.
- A new endpoint group should be created with a descriptive name, and both nodes should be added to the new endpoint group.
- A new virtual wallet is created with a descriptive name, and this needs to both associated with the 2 endpoints, and be the default wallet for the endpoints.
- Both endpoints of the ZDLRA are enrolled through OKV and during the enrollment process a unique enrollment token file is created for each node. It is best to immediately rename the files to identify the endpoint it is associated with using the format <myhost>-okvclient.jar.
- Copy the enrollment token files to the /radump directory on the appropriate host.
#1 Add credential_wallet
racli add credential_wallet
Fri Jan 1 08:56:27 2018: Start: Add Credential WalletEnter New Keystore Password: <OKV_endpoint_password>Confirm New Keystore Password:Enter New Wallet Password: <ZDLRA_credential_wallet_password>Confirm New Wallet Password:Re-Enter New Wallet Password:Fri Jan 1 08:56:40 2018: End: Add Credential Wallet
- New Keystore Password - This password is the OKV endpoint password. This password is used to communicate with OKV by the database, and can be used with okvutil to interact with OKV directly
- New Wallet Password - This password is used to protect the wallet file itself that will contain the OKV keystore password.
#2 Add keystore
racli add keystore --type hsm --restart_db
RecoveryAppliance/log/racli.logFri Jan 1 08:57:03 2018: Start: Configure WalletsFri Jan 1 08:57:04 2018: End: Configure WalletsFri Jan 1 08:57:04 2018: Start: Stop Listeners, and DatabaseFri Jan 1 08:59:26 2018: End: Stop Listeners, and DatabaseFri Jan 1 08:59:26 2018: Start: Start Listeners, and DatabaseFri Jan 1 09:02:16 2018: End: Start Listeners, and Database
#3 Install okv_endpoint (OKV client software)
23 20:14:40 2018: Start: Install OKV End Point [node01]Wed August 23 20:14:43 2018: End: Install OKV End Point [node01]Wed August 23 20:14:43 2018: Start: Install OKV End Point [node02]Wed August 23 20:14:45 2018: End: Install OKV End Point [node02]
Node: node02Endpoint: OnlineNode: node01Endpoint: Online
#4 Open the Keystore
#5 Create a TDE master key for the ZDLRA in the Keystore
Creating Cloud Objects for Copy-to-Cloud
Configure public/private key credentials
- pvt_key_path - Shared location on the ZDLRA where the private key is located
- fingerprint - fingerprint associated with the private key to identify which key to use.
Documentation steps to create new key pair
#1 Add Cloud_key
Tue Jun 18 13:22:07 2019: Using log file /opt/oracle.RecoveryAppliance/log/racli.logTue Jun 18 13:22:07 2019: Start: Add Cloud Key sample_keyTue Jun 18 13:22:08 2019: Start: Creating New KeysTue Jun 18 13:22:08 2019: Oracle Database Cloud Backup Module Install Tool, build 19.3.0.0.0DBBKPCSBP_2019-06-13Tue Jun 18 13:22:08 2019: OCI API signing keys are created:Tue Jun 18 13:22:08 2019: PRIVATE KEY --> /raacfs/raadmin/cloud/key/sample_key/oci_pvtTue Jun 18 13:22:08 2019: PUBLIC KEY --> /raacfs/raadmin/cloud/key/sample_key/oci_pubTue Jun 18 13:22:08 2019: Please upload the public key in the OCI console.Tue Jun 18 13:22:08 2019: End: Creating New KeysTue Jun 18 13:22:09 2019: End: Add Cloud Key sample_key
#2 racli alter cloud_key
Using your own API signing key pair
#1 Add cloud_key
Documentation steps to create a new cloud_user
racli add cloud_user--user_name=sample_user--key_name=sample_key--user_ocid=ocid1.user.oc1..abcedfghijklmnopqrstuvwxyz0124567901--tenancy_ocid=ocid1.tenancy.oc1..abcedfghijklmnopqrstuvwxyz0124567902--compartment_ocid=ocid1.compartment.oc1..abcedfghijklmnopqrstuvwxyz0124567903
- user_name - This is the username that is associated with the cloud_user to unique identify it.
- key_name - This is name of the "cloud_key" identifying the API signing keys to be used.
- user_ocid - This is the Username for authentication. In OCI this is the users OCID, in ZFS, this combines the ocid format with the username on the ZFSSA that owns the share.
- tenancy_ocid - this is the tenancy OCID in OCI, on ZFSSA it is ignored
- compartment_ocid - this is the OCID, on ZFSSA it is the share
Documentation steps to create a new cloud_location
racli add cloud_location--cloud_user=<CLOUD_USER_NAME>--host=https://<OPC_STORAGE_LOCATION>--bucket=<OCI_BUCKET_NAME>--proxy_port=<HOST_PORT>--proxy_host=<PROXY_URL>--proxy_id=<PROXY_ID>--proxy_pass=<PROXY_PASS>--streams=<NUM_STREAMS>[--enable_archive=TRUE]--archive_after_backup=<number>:[YEARS | DAYS][--retain_after_restore=<number_hours>:HOURS]--import_all_trustcert=<X509_CERT_PATH>
--immutable
--temp_metadata_bucket=<metadata_bucket>
- cloud_user - This is the object store authentication information that was created in the previous steps.
- host - This the URL for the object storage location. On ZFS the namespace in the URL is the "share"
- bucket - This is the bucket where the backups will be sent. The bucket will be created if it doesn't exists.
- streams - The maximum number of channels to use when sending backups to the cloud
- enable_archive - Not used with ZFS. With OCI the default TRUE allows you to set an archival strategy, FALSE will automatically put backups in archival storage.
- archive_after_restore - Not used with ZFS. Automatically configures an archival strategy in OCI
- retain_after_restore - Not used with ZFS. Sets the period of time that backups will remain in standard storage before returning to archival storage.
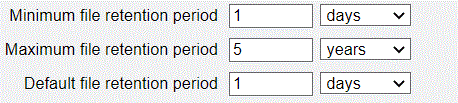
- immutable - This allows you to set retention rules on the bucket by using the <metadata_bucket> for temporary files that need to be deleted after the backup. When using immutable you must also have a temp_metadata_bucket
- temp_metadata_bucket - This is used with immutable to configure backups to go to 2 buckets, and this bucket will only contain a temporary object that gets deleted after the backup completes.
- When configuring backups to go to ZFSSA use the documentation previously mentioned to ensure the parameters are correct.
- When executing this step with ZFSSA, make sure that the default OCI location on the ZFSSA is set to the share that you are currently configuring. If you are using multiple shares for buckets, then you will have to change the ZFSSA settings as you add cloud locations.
- When using OCI for archival ensure that you configure the archival rules using this command. This ensures that the metadata objects, which can't be archived are excluded as part of the lifecycle management rules created during this step.